Cellebrite’s UFED Touch / Physical Analyzer is a portable digital forensic platform that brings comprehensive extraction capabilities anywhere needed such as in the lab, a remote location or in the fields. It extracts data in a closed environment that is separate from other applications, eliminating. UFED Physical Analyzer, UFED Logical Analyzer and Cellebrite Reader v7.29 January 2020 www.cellebrite.com 2 Wickr and Wickr Pro App on iOS This UFED Physical Analyzer version introduces renewed decryption and decoding support for the recent version of the encrypted Wickr app. You can review recovered chat messages, contacts, locations.
UFED Physical Analyzer Crack , the most advanced analysis, decoding and reporting application in the mobile forensic industry. It includes malware detection, enhanced decoding and reporting functions, project analytics, timeline graph, exporting data capabilities and much more.
Advanced capabilities for:
iOS
- Bypassing simple and complex passcode while performing physical and file system extraction on selected devices running iOS 3.0 or higher including iOS 6
- Real-time decryption and decoding of data, applications, and keychain real-time decryption while revealing user passwords
- Advanced decoding of applications
BlackBerry
- Advanced decoding of BlackBerry Messenger (BBM), emails, locations, applications and more
- Real-time decryption of protected content from selected BlackBerry devices running OS 4+ using a given password
Android
- Advanced decoding of all physical extractions performed on devices running any Android versions
- Advanced decoding of applications and application files
GPS
- Portable GPS devices extraction and decoding
- Exclusive – Physical extraction of Tom Tom trip-log files
Cellebrite UFED Physical Analyzer Features
Decoding
Rich set of data
Includes calendar, call logs, contacts SMS, MMS, chats, applications
Highlighted parsed content in the Hex
Highlights the exact position for each decoded content entry, enabling full tractability between the analyzed data and the Hex
Python scripting
Using the Python shell, enhances the capabilities for content decoding
Plugin and chain management
Able to run Python scripts via plugins, and edit and create new decoding chains
Analysis
Malware Detection
Perform on-demand searches for viruses, spyware, Trojans and other malicious payloads in files
Project Analytics
View statistics on communications and identifying relationship strengths
Timeline Graph
Visualize events over time, view distances between events and see the number of events within a defined timespan
Exporting Locations
Export selected latitudes, longitudes, and timestamps to KML reports
Exporting Emails
Export selected emails to EML format
Embedded Text Viewer
View text files including file information, content, and Hex
Advanced search
Based either on open text or specific parameters
Watch list

Ability to highlight information based on predefined list of values
Timeline
Monitor events in a single chronological view
Image carving
Powerful feature used to recover deleted image files and fragments when only remnants are available. Only applicable for physical extraction
All projects field search
Ufed Physical Analyzer Torrent
Quick search within decoded data
Conversation view
View communications between sources in date and time order
Entities bookmarks
Quick reference pointer set to analyzed data item and data file item
Hex viewer
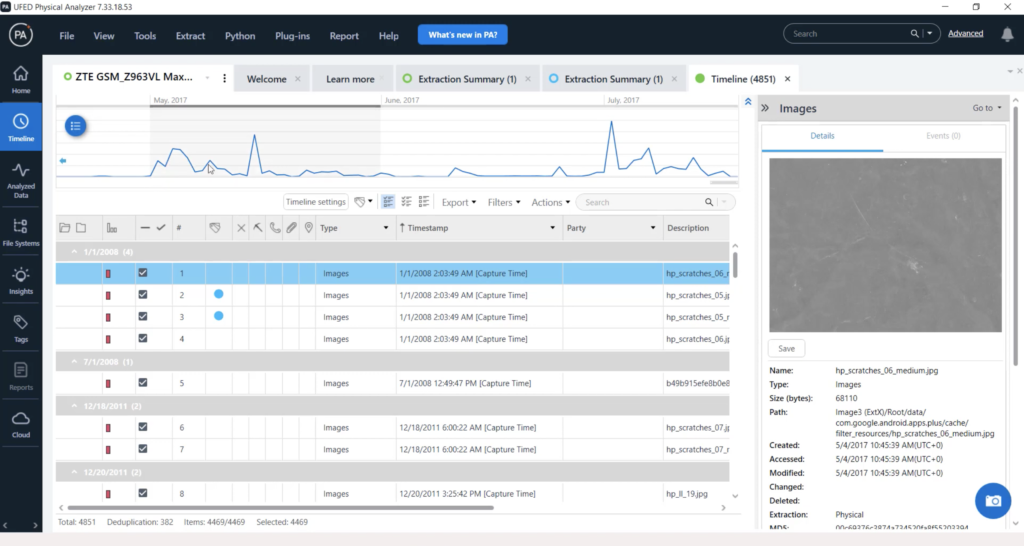
Ufed Physical Analyzer Software
Hexadecimal view of the extracted data enabling advanced search based on multiple parameters, regular expressions and more
Hex bookmarks
Define and save specific locations in Hex data
SQLite databases viewer
Viewing, searching and exporting tables and content (including deleted data) from SQLite database files

Reporting
Report generator
Generate and customize reports in different formats e. g. PDF, HTML, XML and Excel
Confirmation
Hash verification
Ensures the extraction decoded is the same extraction received from UFED device
Software Version
Cellebrite UFED Physical Analyzer 7.44.2.10 – Latest version
Want BUY in Much Lower Price?
Price:250$
E-mail : [email protected]
Also Visit UFED 4PC Software : UFED 4PC
Proof:
UFED Physical Analyzer Free Download
Ufed Physical Analyzer Download Crack
UFED Physical Analyzer Crack and Patch with Serial Number
UFED Physical Analyzer Dongle Emulator
| Type | Private |
|---|---|
| Industry |
|
| Founded | 1999; 22 years ago in Petah Tikva, Israel |
| Founders | Avi Yablonka Yaron Baratz Yuval Aflalo |
| Headquarters | |
Number of locations | 14 (2021) |
| Worldwide | |
Key people |
|
| 800+ (2021) | |
| Divisions | • Cellebrite (Digital Intelligence) • Mobilogy (Commercial & Retailers, Mobile Life Cycle) |
| Website | Cellebrite.com Mobilogy.com |

Cellebrite is an Israelidigital forensics company that provides tools for collection, analysis, and management of digital data. The company is a subsidiary of the Japanese electronics company Sun Corporation.
Overview[edit]
Cellebrite is headquartered in Petah Tikva, Israel. Its two subsidiary companies, Cellebrite USA Corp. and Cellebrite GmbH are respectively based in Parsippany, New Jersey, US, and Munich, Germany. Cellebrite is a fully owned subsidiary of Sun Corporation (JASDAQ: 6736) based in Nagoya, Japan.
In 2017, Cellebrite's Mobile Lifecycle division was rebranded as Mobilogy.[1]
Mobilogy produces hardware and software for phone-to-phone data transfer, backup, mobile applications electronic software distribution, and data analysis tools. Mobilogy products are used by various mobile operators, and are deployed in wireless retail points of sale. Mobilogy works with handset manufacturers to ensure compatibility[clarification needed] before devices are released to the public.[2]
Cellebrite's mobile forensics division was established in 2007 and produces digital forensics and intelligence tools for use by law enforcement, intelligence agencies, military branches, corporate security and investigations, law firms; and private digital forensic examiners.[2]
History[edit]
Cellebrite was established in Israel in 1999 by Avi Yablonka, Yaron Baratz, and Yuval Aflalo.[citation needed] Cellebrite first manufactured hardware and software that offered a compressive phone-to-phone data transfer devices, contact synchronization and content transfer tools for mobile phones, intended for use by wireless carrier sales and support staff in retail stores.
Ufed Physical Analyzer Free Download
Initially, Cellebrite's commercial products were used as a tool for migration from IS-95 (CDMA) enabled mobile phones to the GSM standard. Later, Cellebrite Wireless Carriers & Retailers' Universal Memory Exchanger (UME) gained additional data extraction and transfer capabilities, as well as additional mobile phone diagnostics, backup, and application management and delivery.[citation needed]
In 2007, Cellebrite established an independent division targeted at the mobile forensics industry. The division first introduced mobile forensics products, under the family brand name 'Universal Forensic Extraction Device' (UFED), which have the ability to extract both physical and logical data from mobile devices, including the ability to recover deleted data and decipher encrypted and password protected information.[citation needed]
Also in 2007, Cellebrite was acquired by FutureDial Incorporated and one of its major shareholders, Sun Corporation in Japan.[3] Today[as of?] Sun Corporation is Cellebrite's largest shareholder. In 2019 Israeli Growth Partners (IGP) invested $110 million in Cellebrite.[4]
In 2020, Cellebrite acquired BlackBag Technologies, a forensics company with a focus on computer forensics. The acquisition allowed Cellebrite to expand its digital intelligence solution offerings to include data collection tools from computers.[5]
In 2021, Cellebrite announced that they entered into a definitive business combination agreement and plan of merger with TWC Tech Holdings II Corporation. Once completed, Cellebrite will become a publicly listed company on the Nasdaq under the new ticker symbol, “CLBT”; the pro forma implied equity value of Cellebrite post-merger is expected to be approximately $2.4 billion.[6]
Law enforcement assistance[edit]
In April 2011, the Michigan chapter of the American Civil Liberties Union questioned whether Michigan State Police (MSP) troopers were using Cellebrite UFEDs to conduct unlawful searches of citizens' cell phones.[7] Following its refusal to grant the ACLU of Michigan's 2008 Freedom of Information Act request unless the organization paid $544,000 to retrieve the reports, MSP issued a statement claiming that it honored the Fourth Amendment in searching mobile devices.[8]
In March 2016, it was reported that Cellebrite offered to unlock an iPhone involved in the FBI–Apple encryption dispute.[9] Later, after the FBI announced it had successfully accessed the iPhone thanks to a third party. A press report claimed Cellebrite had assisted with unlocking the device,[10] which an FBI source denied.[11]
A 2017 data dump suggests Cellebrite sold its data extraction products to Turkey, the United Arab Emirates and Russia.[12]
On 16 September 2020, Haaretz reported how Cellebrite had provided Saudi Arabia with mobile phone hacking services. The staff at Cellebrite demanded the Saudis to send a government representative to meet one of their employees at the King Khalid International Airport in Riyadh. Following the demand, a representative of Cellebrite traveled to Riyadh in November 2019 for an hacking attempt on a phone in the possession of a Saudi Justice Ministry employee. The Cellebrite representative called for the authorities to let him pass through passport control without getting his passport stamped or his electronic equipment being checked, while remaining only under his possession. The hacker was supposed to head to an isolated hotel room from the airport, where the process was planned to be executed without any electronic surveillance. The Cellebrite representative then returned to the Riyadh airport to fly back to London.[13]
U.S. Immigration and Customs Enforcement[edit]
In 2017, Cellebrite entered into a contract with U.S. Immigration and Customs Enforcement (ICE) for $2.2 Million.[14] On June 24, 2019, another contract was signed with ICE for between $30 and $35 million. The 2019 contract was for “universal forensic extraction devices (UFED), accessories licenses, training and support services” for one year, with an option to extend for up to five years.[15][16]
Hong Kong[edit]
In August 2020, MIT Technology Review reported that Cellebrite sold its services to the Hong Kong Police Force for use in unlocking phones of detained demonstrators during the 2019–20 Hong Kong protests.[17] As of October 7, 2020, the company announced that it would stop selling its solutions and services to customers in Hong Kong and China as a result of a change in U.S. regulations.[18]
Eastern Europe[edit]
Cellebrite's UFED program was used to persecution of opposition in Belarus and Russia. In March 2021 after finding out that technology was used in the Lyubov Sobol affair Jerusalem activist has filed a lawsuit against the company in the Israeli Supreme Court. Shortly after the company announced the terminaton of partnership with Russia.[19]
Security breaches[edit]
Ufed Physical Analyzer Manual
On 12 January 2017, it was reported that an unknown hacker had acquired 900 GB worth of confidential data from Cellebrite's external servers. The data dump includes alleged usernames and passwords for logging into Cellebrite databases connected to the company's my.cellebrite domain, and also contains what appear to be evidence files from seized mobile phones, and logs from Cellebrite devices.[20] The dumped data suggested Cellebrite sold its data extraction products to countries such as Turkey, the United Arab Emirates and Russia.[12]
Vulnerability report by Signal[edit]
In 2021, Moxie Marlinspike, creator of the encrypted messaging app Signal, released a blog post on the app's website detailing a number of vulnerabilities in Cellebrite's UFED and Physical Analyzer software that allowed for arbitrary code execution on Windows computers running the software. One exploit he detailed involved the UFED scanning a specially formatted file which could then be used to execute arbitrary code on the computer running the UFED. Marlinspike wrote that the code could then '[modify] not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way'.[21] Marlinspike also found that Cellebrite software was bundled with out-of-date FFmpegDLL files from 2012, which lacked over 100 subsequent security updates. Windows Installer packages, extracted from the Windows installer for iTunes and signed by Apple, were also found, which he said raised legal concerns.[22] Cellebrite issued a statement in response, saying the company 'is committed to protecting the integrity of our customers’ data, and we continually audit and update our software in order to equip our customers with the best digital intelligence solutions available.'[23] The report by Signal followed an announcement by Cellebrite in 2020 that it had developed technology to crack encrypted messages in the Signal app, a claim the company later retracted and downplayed.[24][25]
The announcement by Marlinspike prompted Cellebrite to patch some of the vulnerabilities found by Signal and to remove full support for analyzing iPhones,[26][27] and raised questions about the integrity of data extracted by the software.[28][29]
References[edit]
Ufed Physical Analyzer Download
- ^'Mobilogy Rebrand Press Release'(PDF). Archived from the original(PDF) on July 3, 2018. Retrieved July 3, 2018.
- ^ ab'Cellebrite Customers'. Retrieved April 9, 2017.
- ^'FutureDial and Sun Corporation Acquire Cellebrite'. ThomasNet. Retrieved July 19, 2012.
- ^Rabinovitch, Ari. 'Israeli digital forensics firm Cellebrite gets $110 mln IGP investment'. Reuters. Thomson Reuters. Retrieved July 8, 2020.
- ^Miller, Chance. 'Cellebrite expands to computers with $33M acquisition of BlackBag Technologies forensics firm'. 9to5 Mac. Retrieved July 8, 2020.
- ^'Cellebrite to list on Nasdaq at $2.4b valuation through SPAC'. Globes. August 4, 2021. Retrieved April 22, 2021.
- ^Sullivan, Bob. 'Gadget gives cops quick access to cell phone data'. MSNBC. Archived from the original on April 23, 2011. Retrieved April 21, 2011.
- ^Heussner, Ki Mae. 'Michigan Police Use Device to Download Cellphone Data; ACLU Objects'. ABC News. Retrieved June 8, 2012.
- ^'San Bernardino shooting:Israeli company is helping the FBI, reports say'. The Press-Enterprise. March 23, 2016. Retrieved March 23, 2016.
- ^Benmeleh, Yaacov. 'FBI Worked With Israel's Cellebrite to Crack iPhone'. Bloomberg News. Retrieved April 1, 2016.
- ^'FBI's Comey, officials discount two iPhone hack theories'. USA TODAY. Retrieved April 1, 2016.
- ^ abCox, Joseph (January 12, 2017). 'Cellebrite Sold Phone Hacking Tech to Repressive Regimes, Data Suggests'. Motherboard. Retrieved July 3, 2017.
- ^'Revealed: Israeli Firm Provided Phone-hacking Services to Saudi Arabia'. Haaretz. Retrieved September 16, 2020.
- ^Fox-Brewster, Thomas. 'US Immigration Splurged $2.2 Million On Phone Hacking Tech Just After Trump's Travel Ban'. Forbes. Retrieved September 13, 2019.
- ^Montgomery, Blake (September 11, 2019). 'ICE Has a New $30M Contract With Israeli Phone Cracking Company Cellebrite'. Retrieved September 13, 2019.
- ^Pelt, Mason (September 13, 2019). 'ICE Will Pay Up To 35M To Cellebrite For Phone Hacking Tech'. Internet News Flash. Retrieved September 13, 2019.
- ^O'Neill, Patrick Howell (August 25, 2020). 'Israeli phone hacking company faces court fight over sales to Hong Kong'. MIT Technology Review. Retrieved August 30, 2020.
- ^Shmuklyer, Olga (October 7, 2020). 'Cellebrite to Stop Selling Its Digital Intelligence Offerings In Hong Kong & China'. Cision PR Newswire. Retrieved October 9, 2020.
- ^«Через 6 часов они ушли из России». Юрист вынудил израильских взломщиков смартфонов разорвать отношения с российскими силовиками
- ^'Hacker Steals 900 GB of Cellebrite Data'. Motherboard.
- ^Marlinspike, Moxie (April 21, 2021). 'Exploiting vulnerabilities in Cellebrite UFED and Physical Analyzer from an app's perspective'. Signal Blog. Retrieved April 22, 2021.
- ^Goodin, Dan (April 21, 2021). 'In epic hack, Signal developer turns the tables on forensics firm Cellebrite'. Ars Technica. Retrieved April 22, 2021.
- ^Kan, Michael (April 21, 2021). 'iPhone Hacking Device From Cellebrite Is Rife With Exploitable Flaws, Says Signal'. PCMag. Retrieved April 22, 2021.
- ^'Encrypted chat app Signal alleges flaws in Cellebrite equipment'. Reuters. April 21, 2021. Retrieved April 22, 2021.
- ^'Signal slams Cellebrite security company over alleged security holes'. BBC News. April 22, 2021. Retrieved April 23, 2021.
- ^Lovejoy, Ben (April 27, 2021). 'Cellebrite Physical Analyzer no longer fully available for iPhones following Signal blog post'. 9to5mac. Archived from the original on April 28, 2021. Retrieved April 28, 2021.
- ^Franceschi-Bicchierai, Lorenzo; Cox, Joseph (April 27, 2021). 'Cellebrite Pushes Update After Signal Owner Hacks Device'. Motherboard. Archived from the original on April 28, 2021. Retrieved April 28, 2021.
- ^Ropek, Lucas (April 27, 2021). 'Signal's Cellebrite Hack Is Already Causing Grief for the Law'. Gizmodo. Archived from the original on April 28, 2021. Retrieved April 28, 2021.
- ^Yaron, Oded; Benjakob, Omer (April 25, 2021). ''Stop Using Cellebrite': Israeli, U.K. Police Urged to Stop Using Phone-hacking Tech'. Haaretz. Archived from the original on April 28, 2021. Retrieved April 28, 2021.